IT uses
Web 2.0

Communication and collaboration
External social netweorking sites
Specialized forums
Interoperability
Information sharing
Downloading

P2P
Mobile Internet
PDAs
3G

apps

GPS
Identity theft
Internet security
Cybercrime
Phishing
spyware
Information
encrypted
coded
Privacy and confidentiality
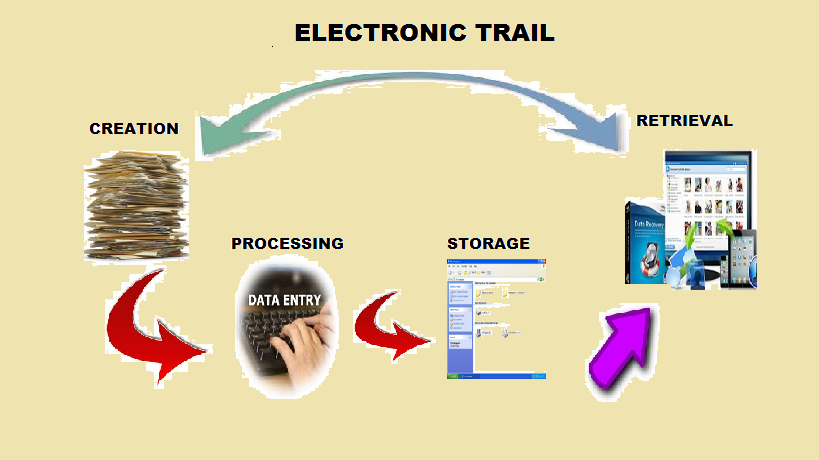
Electronic trail
personal details
law enforcement agencies
surveilliance
snoop into
infiltrating

Hackers
Virus
hijack
infected
malicious software/malware
E-commerce
B2B
trading hub
reverse auctions
consortium e-marketplace
B2C
pure-play
bricks-and-mortar outlets
clicks-and-mortar outlets
price comparison sites

E-procurement
Intellectual property
Illigal downloading
Copyright infringement
Encryption
Digital watermarks
DRM