Authentication 思维导图 - 公共图库
探索我们广泛的authentication思维导图公共集合,这些思维导图由世界各地的Mulquatro用户创建。在这里,你可以找到所有与authentication相关的公开图表。你可以通过查看这些示例获得一些灵感。有些图表还允许你复制和编辑。这种灵活性使您可以将这些思维导图用作模板,从而节省时间,并为您的工作提供一个强有力的起点。一旦你公开了自己的图表,你就可以为本图库贡献自己的图表,你也可以成为其他用户的灵感来源,并在这里得到介绍。

Routings
由CCNA CCNA


CISSP: Access Control Systems and Methodology
由Walkowska Anna

MicroServices
由Mike Ton

Virtual Private Netw
由sihui lau

IT Security Terms
由Usama Amin


MS302-303 Section 1: Planning Network Infrastructure
由James Herbert
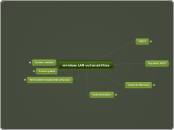

wireless LAN vulnerabilities
由nursyafeera azeera

TPM (TimUR Performance Management)
由Alfiah Khoirunisa
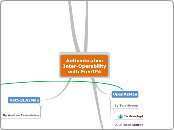

Authentication inter-operability FreeIPA / AzMan
由ericdes (Eric)

Edgar Collins and the new Cezanne
由kinda tarek

A Paul Cézanne painting
由ALi Abd El-Latif

Remote Access
由sihui lau

Auth
由Ivan Kayzer

Authentification/De-authentifiction of Artwork
由Olivia Quinn

5c
由soha osman


Classwork # 8
由Darya Fatih

iis
由Behnam shiri

MS301 Obj 6. Implementing, Managing, and Troubleshooting Network Protocols and Services
由James Herbert

Sample Mind Map
由Octavio Hernandez

BangAli
由Yovi Oktofianus

AD Polling Mode
由Nestor Catacora


Access Contol
由Kenneth Gourlay


As Light Meets Matter: Art Under Scrutiny
由Dalia Kamar


As Light Meets Matter: Art Under Scrutinity
由Farah Anwar

Virtual Private Netw
由sihui lau

Assi 4a
由Khaled Mohsen

Mental Health
由Suresh kumar Mukhiya

YS
由Ken Reid

AD, OD and Cent Workflow
由Cheryl Lynn
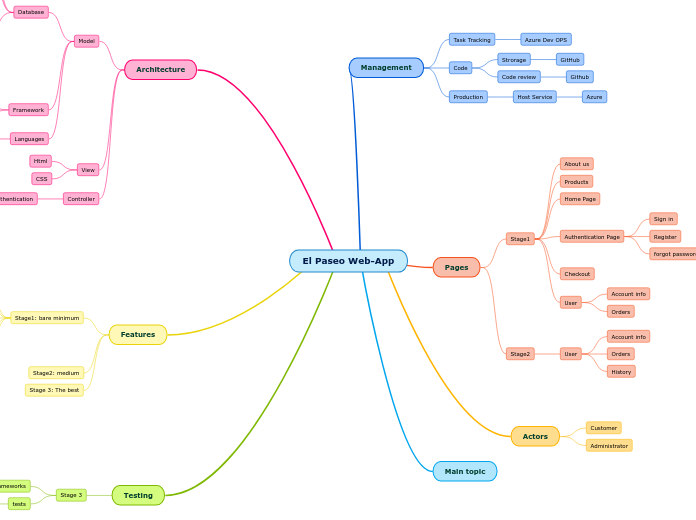

El Paseo Web-App
由Geraldine Davila


InfrastructureSecurityComponents
由Iben Rodriguez

Authenticating Famous Works of Art
由Clarissa Pharr
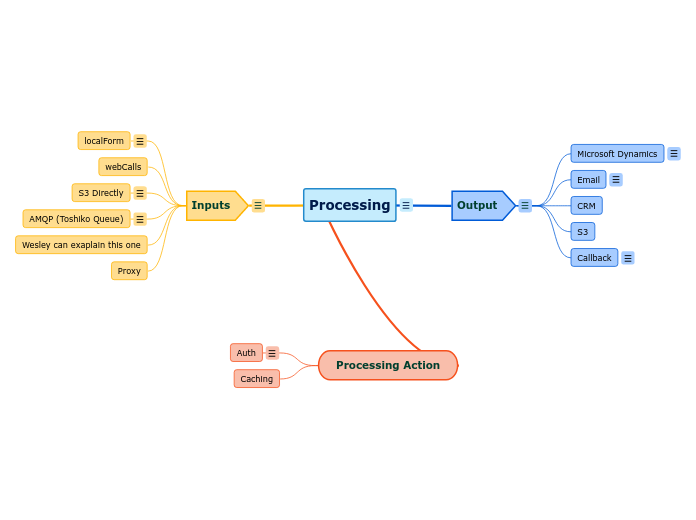

Processing
由Taibi Aymane
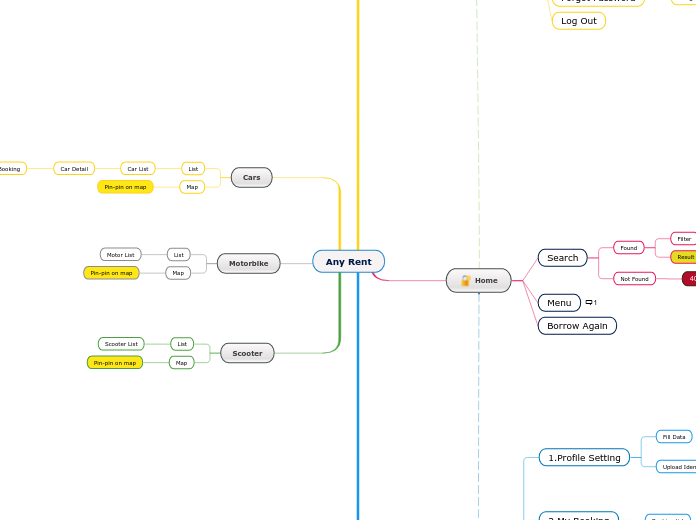

Any Rent
由Syahdan Hidayat
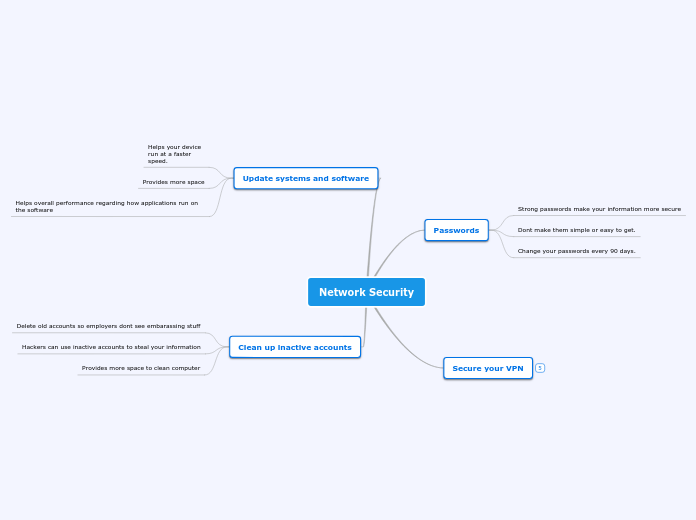

Network Security
由Jake Kilgore

Sample Mind Map
由lama hazaa

Art under scrutiny
由Noha Marei
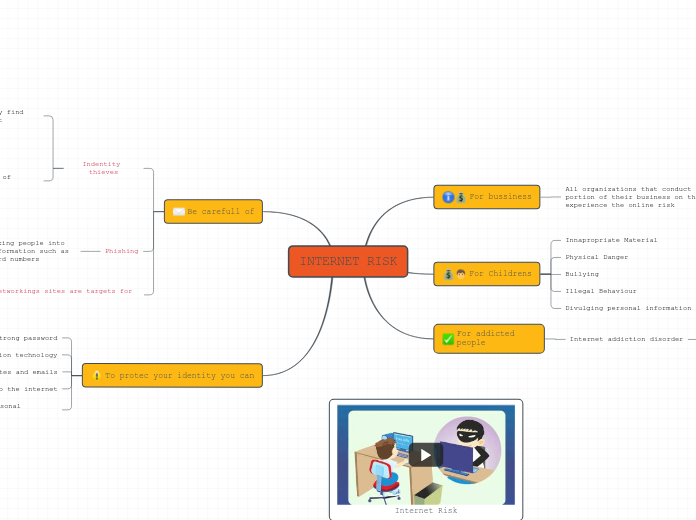

INTERNET RISK2
由Shakirs Franco
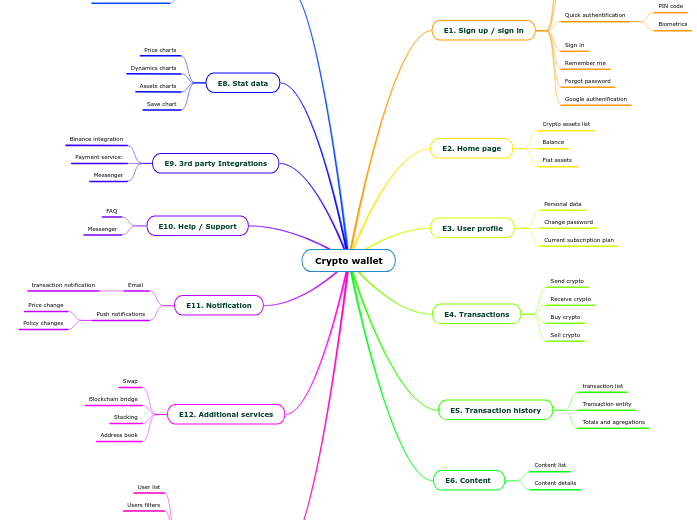

Crypto wallet
由Volodymyr Ponomarenko
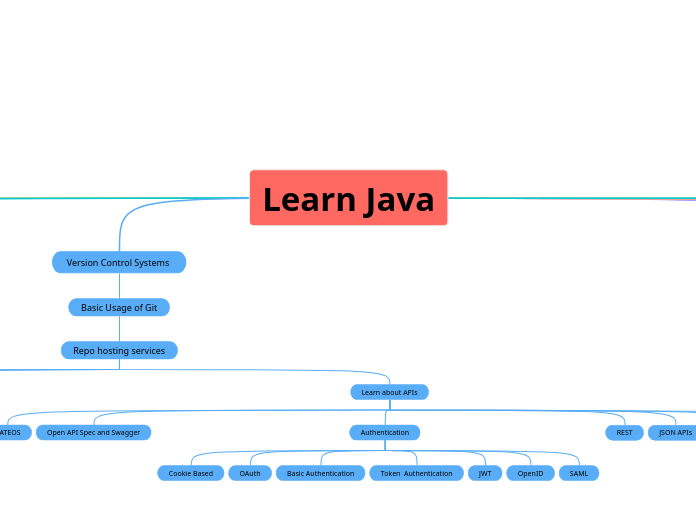

Learn Java
由Артур Базанов

Mind Map Projek Onboard Sirus
由Aditya Wibowo
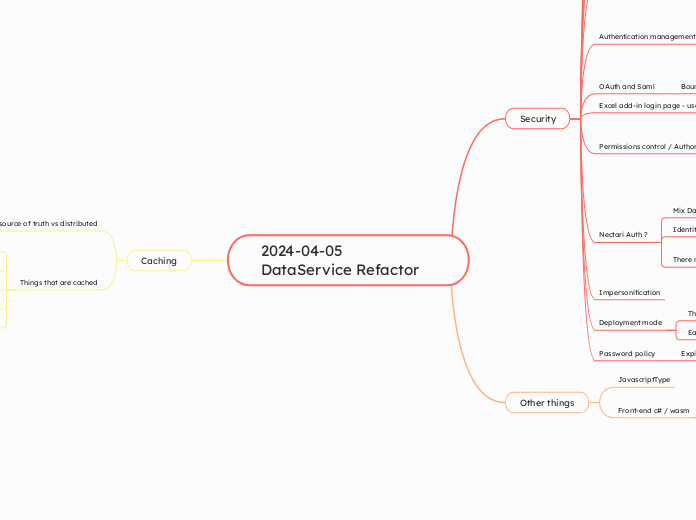

2024-04-05 DataService Refactor
由Samy Sarem
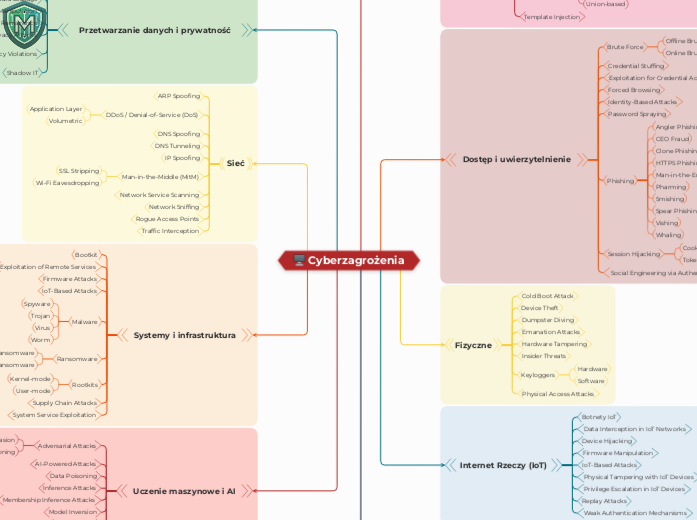

Cyberzagrożenia
由dr inż. Michał Malinowski
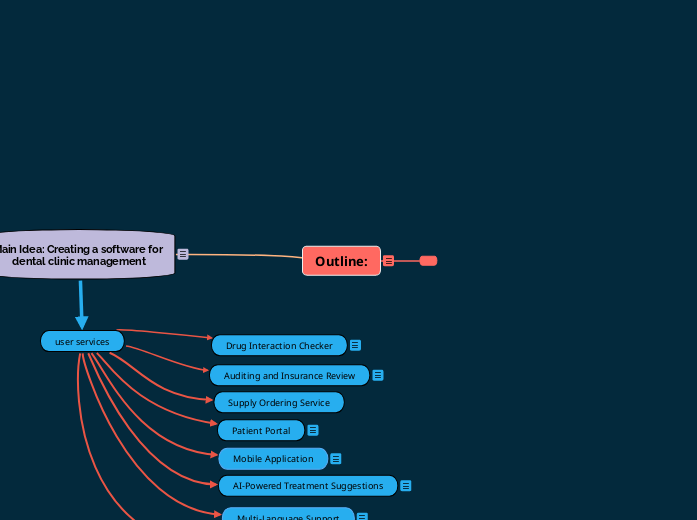

Outline: - Copy
由code clinic
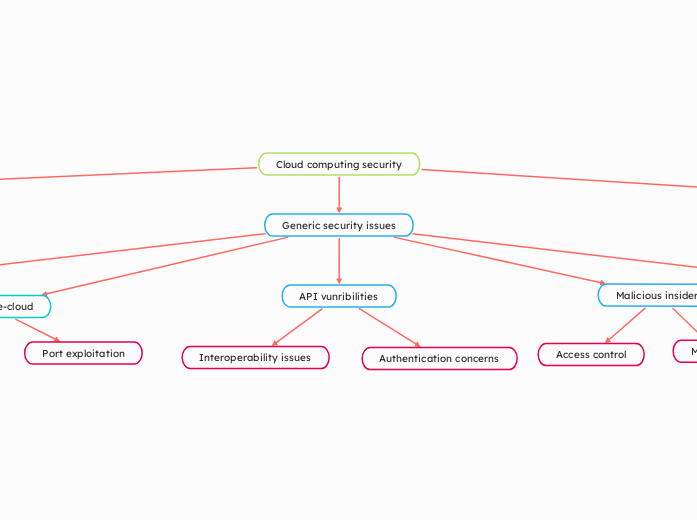

Cloud computing security
由Jack Barnes



